What is Multi-factor Authentication?
Multi-factor authentication (MFA) refers to a layered end-user verification strategy to secure data and applications by requiring a user to submit various combinations of two or more credentials to gain access to a system or service.
There are three components of MFA:
- Something you know — Password, PIN, or passphrase
- Something you have — OTP (one-time password), verification code, or hard or soft security token
- Something you are — Biometrics (fingerprint, facial scan, or iris scan)
The Microsoft Authenticator App is traditionally used with a mobile device such as a cell phone for push notifications. This helps you sign into your accounts when you’re using a two-step verification process.
The standard two-step verification method involves two factors: One factor typically being your username and password and a second factor such as a PIN, code or personal biometric.
How Does MFA Work?
Mobile push-notification-based MFA uses “push” notifications to alert a user to review a new MFA
authentication request. The login flow is:
- The user enters their username and password to authenticate (first factor)
- The identity platform sends a signal to the app on the user’s phone/mobile device, which generates a notification
- The user opens and accepts the prompt to approve the request (second factor)
Incorporating both factors makes the sign in process safe and secure, however, malicious cybercriminals continue to find ways to try to bypass MFA. With the adoption of two factor, MFA fatigue spamming attacks have gain popularity and become more prevalent by cybercriminals.
What is MFA Fatigue?
MFA fatigue is a technique where a cybercriminal attempts to gain access to sensitive information by bombarding their victims with repeated two-factor authentication push notifications in hopes of tricking them into authenticating their login attempts.
Cybercriminals will commonly use stolen login credentials obtained from various social engineering methods, including phishing attacks, malware or leaked credentials from data breaches. Cybercriminals who have obtained a user’s password will enter it into an identity platform that uses mobile push-notification-based MFA to generate hundreds of prompts on the user’s device over a short period of time.
The goal is to spam victims to the point where they are annoyed by the constant notifications and will approve one so it will stop. Although it may seem harmless, by doing so, the attacker has effectively bypassed MFA and now has access to their victim’s information and critical infrastructure.
This attempt can be successful, especially when the target victim is distracted or overwhelmed by the notifications or misinterprets them as legitimate authentication requests.
Recent studies show that about 1% of users will accept a simple approval request on the first try. That’s why it’s critical to ensure that users must enter information from the login screen and that they have more context and protection.
What is Changing with the Authenticator App?
Microsoft will enable number matching requirements within the Microsoft Authenticator App by default for all users starting on February 27, 2023.
Number matching is a security upgrade that will discourage MFA fatigue as each push notification generates a unique set of numbers for every login request. Number matching is a setting that forces the user to enter numbers from the identity platform into their app to approve the authentication request.
How Does Number Matching Work?
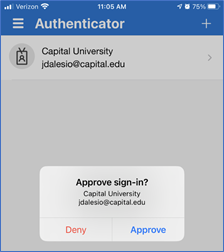
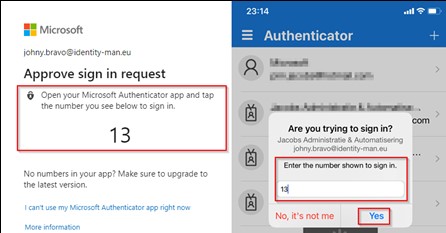
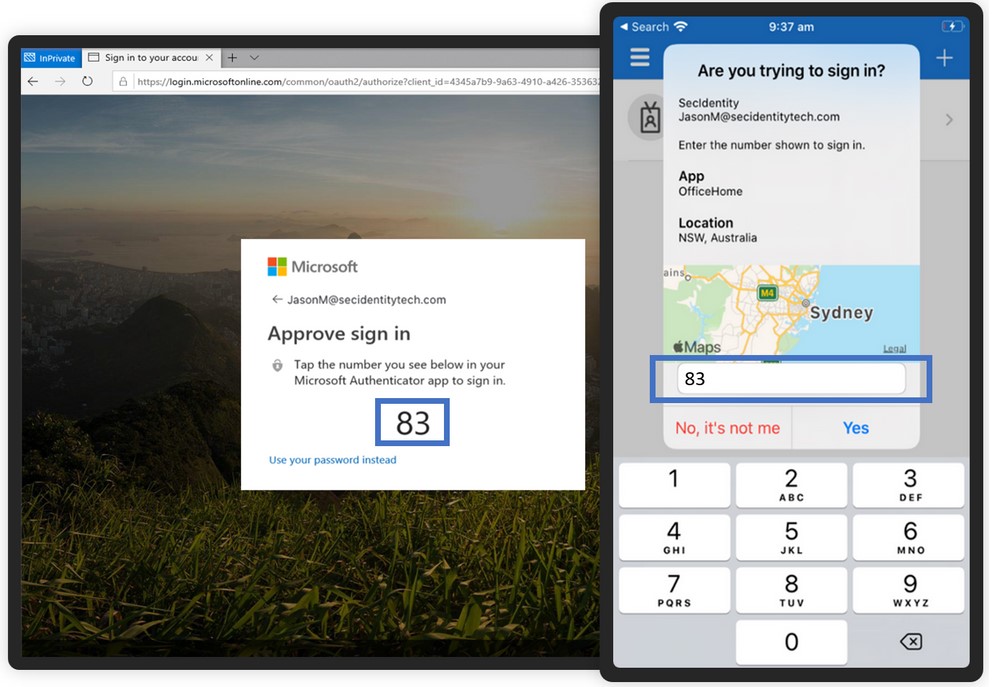
When a user responds to an MFA push notification using Microsoft Authenticator, they will be presented with a number that the user will be required to type into the App during the sign-in process to complete the approval.
Depending on how Microsoft Authenticator App is configured and the operating system of your mobile device may generate an experience similar to the examples below:
Basic Number Matching: When a user responds to an MFA push notification using Microsoft Authenticator, they will be presented with a number which they need to type into the Authenticator app to complete the approval process.
Geographic Location with Number Matching: When a user receives a Passwordless phone sign-in or MFA notification in the Authenticator app, they’ll see the sign-in location (based on their IP) and number matching information. Type the number that was pushed to your mobile device into the Microsoft Authenticator app to complete the sign in approval process.
Don’t have the Authenticator App?
Download and follow these instructions: Download Microsoft Authenticator App Here